Achieve unmatched scalability through the power of Kubernetes.
As a Cloud Native Foundation member and a Kubernetes Certified Service Provider (KCSP), Centroid has been integral to the design and launch of Kubernetes environments for numerous enterprises, including multiple Fortune 500 companies. We bring unmatched expertise to projects of all sizes, empowering organizations to achieve scalability and flexibility through Kubernetes. Our full suite of services—design, implementation, support, training, and security—transforms infrastructure into highly available and resilient environments.
With offerings like Assessments, Enterprise Solutions, and Managed Services, Centroid enables you to harness Kubernetes for seamless deployment, automated scaling, and efficient application management in today’s dynamic cloud landscape.

Discover the Kubernetes advantage: Ask yourself these 3 questions
As businesses consider migrating their applications to Kubernetes, it’s crucial to assess whether this platform aligns with their specific needs. Here are key questions to guide your decision-making process:
- Are you struggling to scale efficiently without over-provisioning or facing downtime from manual workload management?
- Is managing apps across on-prem and cloud environments while avoiding vendor lock-in a challenge?
- Are long development timelines and inefficient workflows slowing your ability to deliver features and updates quickly?
If you answered yes to any of these questions, Kubernetes could be the ideal solution for your business. Given Kubernetes’ extensive ecosystem and diverse approaches, we offer a specialized service – the Kubernetes Assessment – where our experts analyze your current setup, providing tailored advice to optimize your utilization of this powerful platform.
Decoding Kubernetes: Explore Assessments, Enterprise Solutions, and Managed Services with our Datasheets
Kubernetes Services
Explore our comprehensive Kubernetes services below—designed to ensure your infrastructure becomes a highly available, scalable, and secure Kubernetes environment. From implementation to monitoring, support, and security, our solutions empower your team to focus on innovation while we optimize performance and reliability.
Implement
Centroid works with clients to design and deploy Kubernetes clusters, both on-premise and in the cloud, automating software deployments. Our SREs have extensive experience with cloud providers like Oracle Cloud Infrastructure, AWS, Azure, Google Cloud, and on-premise environments such as Oracle EBS, VMware and Bare Metal.
Our Approach
-
- Cluster Setup: We build clusters from scratch or use managed services like OKE, GKS, EKS, and AKS, based on your needs.
- CI/CD Automation: Centroid automates software deployments, enabling quick, reliable updates with minimal manual effort.
- Persistent Storage: We integrate persistent storage solutions like Azure Managed Disks and AWS Elastic Block Store with Kubernetes for data consistency.
- Secure Traffic Ingressing: Our SREs ensure secure, encrypted traffic using tools like Istio and Linkerd.
Kubernetes Cloud
Run your workloads efficiently on our secure, compliant, managed Kubernetes Cloud. Centroid’s Kubernetes Cloud ensures your business applications can be safely run in the cloud. We work to help keep your data secure with nightly offsite backups, end-to-end encryption, and real-time monitoring and alerting. In addition, our team of site reliability engineers is available 24×7 with tight SLAs to ensure availability in the event of incidents.
What We Offer
-
- End-to-end encryption: Encryption of traffic from your customer’s machine to load balancers, to the applications themselves, as well as encryption between applications.
- Change management: Employed in our production environments with all changes being tracked and managed, preparing your organization to be fully compliant.
- Nightly offsite backups: Regular backups of your code into cold storage and nightly offsite backups of your data, including file storage and SQL databases.
- Self-healing infrastructure: Automatically reboots, redeploys, scales, or shifts load as required to ensure your application remains alive and responsive.
- Continuous Integration and Continuous Delivery: Automated software delivery for your development team, from writing code to deploying test environments and promoting to production, ensuring secure and efficient workflows.
Security
Centroid leverages proprietary tools to scan, audit, and strengthen the security of your Kubernetes clusters and applications. While setting up Kubernetes on OCI (OKE), AWS (EKS), Google Cloud (GKS), Azure (AKS), or other clouds is straightforward, effective security requires expertise. Centroid implements access controls, firewalls, encryption, and network policies to safeguard your Kubernetes environment, and we train your team on essential security practices.
Our Security Services
-
- Pod Security Policies: Our scans ensure Pod Security Policies are configured to prevent privilege escalation and mitigate key Kubernetes threats.
- Host & Container Scanning: We secure Kubernetes nodes and container images by scanning for unpatched vulnerabilities, ensuring your environment remains up to date.
- Encryption: Centroid implements end-to-end encryption for secure communication across load balancers, Kubernetes applications, and data centers.
-
Access Controls: Using tools like Active Directory, Vault, or Rancher, Centroid enforces granular access controls to protect user privileges and data.
Monitor and Support
-
- Metric Scraping & Aggregation: We use tools like Prometheus and New Relic to scrape metrics and detect system issues or erratic behavior.
- Escalation Procedures: Centroid creates customized runbooks for each client, defining support protocols and how to handle common infrastructure problems.
- Log Aggregation: We aggregate server and application logs to efficiently search for exceptions, errors, and stack traces when diagnosing issues.
- 24/7 Support: Our global support team, staffed with CKA-certified DevOps engineers, is available around the clock to resolve any incidents.
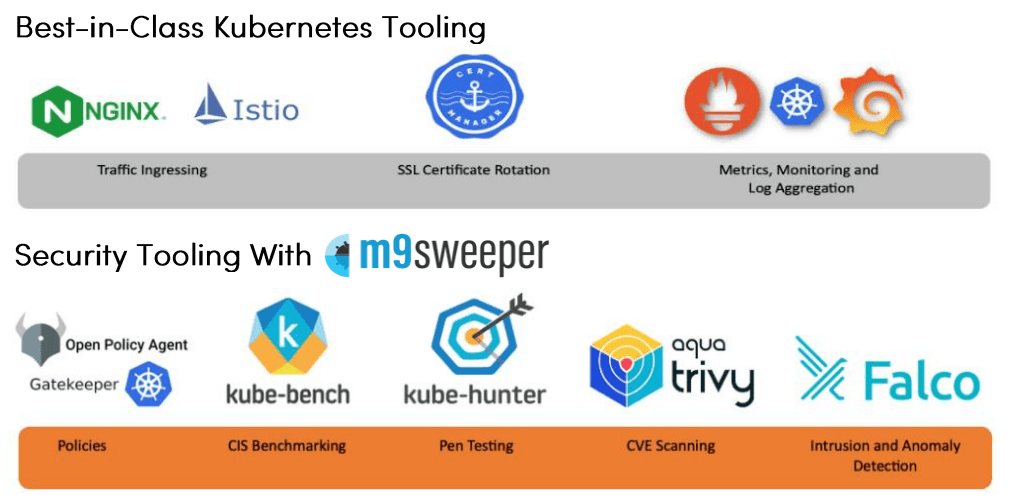
Kubernetes Stack: Built for peak performance and security
To optimize the performance of your Kubernetes cluster and its applications, we implement a robust suite of monitoring, security, and compliance tools. This ensures continuous security and monitoring, reinforcing the resilience and efficiency of your cluster around the clock.
m9sweeper takes Kubernetes security a step further, empowering your Operations team to identify and mitigate risks efficiently. It scans applications and OS dependencies for known vulnerabilities (CVEs), enforces cluster-wide CIS Benchmarking compliance, and analyzes individual pods with KubSec—making security simple, fast, and effective.
Explore how m9sweeper can strengthen your Kubernetes environment. Download the datasheet for a complete overview of its capabilities.
Enabling Digital Transformation with Oracle Cloud and Kubernetes
Centroid harnessed the capabilities of Oracle Cloud and Kubernetes to deliver a scalable and cost-efficient solution to a customer. Following the implementation, our customer can now scale data science workloads in a matter of seconds, a stark contrast to the days or weeks it used to take. Our team transformed the customer’s business but also paved the way for sustainable, long-term growth by enhancing security, reducing total ownership costs, and improving the CI/CD pipeline.
Kubernetes vs. VM: Making the Right Choice for Your Business
What’s the difference between Kubernetes and traditional VM deployments, and which one is the best for my business? Ajay Arora, a Centroid Managing Partner and CTO, and Jacob Beasley, Director of DevOps, answer all this and more in this podcast.
Take the next step
Contact us today for more information about our Kubernetes services.



